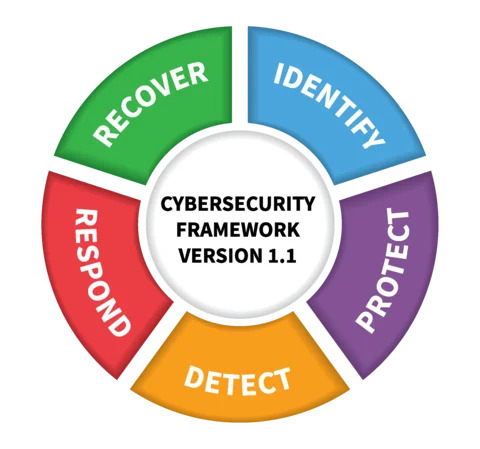
Updated OWASP Mobile Top 10 for 2024
The list of OOWASP Mobile Top 10 for 2024 is a collection of the ten most commonly reported vulnerabilities found in mobile applications. The information is gathered from various organizations worldwide, all of which are affiliated with the same industry. What does OWASP stand for? The OWASP Foundation stands as a beacon in the realm