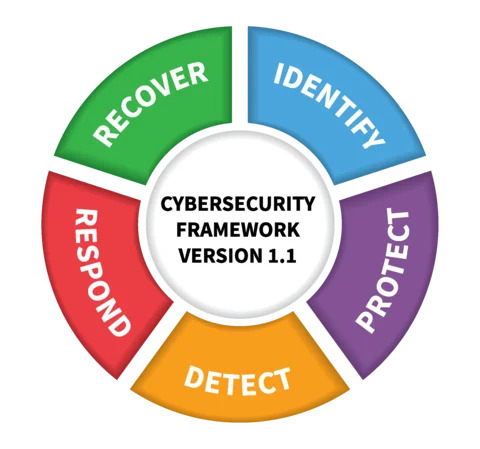
Malicious backdoor spotted in Linux
Linux, the free, open-source operating system, has always been hailed for its robust security. However, a recently Malicious backdoor spotted in Linux, XZ Utils, has led to a surge in cybersecurity concerns. The backdoor, identified as liblzma and designated as CVE-2024-3094, was found in the beta releases of major Linux distributions. This article aims to shed