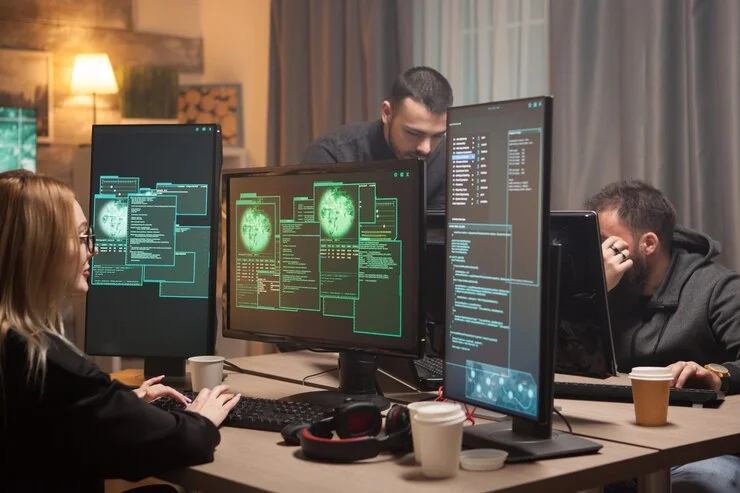
why do we need penetration testing
Most of companies ask why we need penetration testing, Vulnerability Assessment and Penetration Testing has become a top priority for companies of all sizes. The ever-evolving threat landscape poses significant risks to sensitive data and network infrastructure. To mitigate these risks, organizations must adopt a proactive approach towards identifying and addressing vulnerabilities. This is where