The Department of Defense (DoD) has released a dod zero trust strategy aimed at achieving an enterprise-wide zero trust cybersecurity framework by 2027. The dod zero trust strategy outlines the strategic vision, assumptions, principles, and goals for implementing a robust zero trust approach across the DoD Information Enterprise.
The DoD’s zero trust strategy is based on key principles, including a cultural shift, infrastructure modernization, global collaboration, and stakeholder buy-in. The strategic objectives cover four areas: promoting a zero-trust culture, securing DoD information systems through zero trust implementation, accelerating zero trust technologies, and enabling zero trust capabilities across the department. This step-by-step guide explores the DoD’s zero trust approach, providing insights into its implementation, challenges, and real-world examples of zero trust policies and networks within the Department of Defense zero trust strategy.
What is the definition Zero-Trust Strategy ?
Zero Trust is a revolutionary cybersecurity approach that challenges traditional perimeter-based security models. Instead of assuming trust based on network location, dod zero trust strategy operates on the principle of “never trust, always verify.” This strategy denies access to an enterprise’s digital resources by default and grants authenticated users and devices tailored, siloed access to only the applications, data, services, and systems they need.
The core principles of the Zero Trust model are:
- Continuous Verification: User identities and roles are continuously verified, regardless of their location (inside or outside the network perimeter).
- Limiting the “Blast Radius”: The network is segmented into smaller, discrete zones to contain potential threats and limit the impact of a breach.
- Automating Context Collection and Response: User and device context, such as location, device posture, and behavior, is continuously collected and analyzed to inform access decisions and automate responses.
Key Benefits of Zero Trust
The Zero Trust approach offers several benefits, including:
- Protection of Sensitive Data: By granting access only to authorized users and devices, sensitive data is better protected from unauthorized access and potential breaches.
- Support for Compliance Auditing: The continuous verification and logging of user and device activities facilitate compliance auditing and reporting.
- Lower Breach Risk and Faster Detection: The segmented network architecture and continuous monitoring help contain threats and enable faster detection of anomalies or breaches.
- Improved Visibility into Network Traffic: The Zero Trust model provides better visibility into network traffic, enabling more effective monitoring and control.
- Better Control in Cloud Environments: The Zero Trust approach is well-suited for securing cloud environments, where traditional perimeter-based security models may not be as effective.
Key Components of Zero Trust
To implement a Zero Trust strategy, organizations typically leverage advanced technologies such as:
- Risk-based Multi-Factor Authentication (MFA): Robust authentication mechanisms that consider user and device context to determine the appropriate level of access.
- Identity Protection: Solutions that protect user identities from compromise and enable secure access to resources.
- Next-Gen Endpoint Security: Advanced endpoint protection platforms that continuously monitor and secure devices, regardless of their location.
- Cloud Workload Security: Solutions that secure cloud workloads and enforce Zero Trust policies across cloud environments.
Example Zero Trust Implementation
Microsoft’s Zero Trust Approach
- Microsoft’s zero trust model focuses on securing corporate services, devices, and device management via Microsoft Intune, spanning four phases:
- Verify Identity: Ensuring user identities are properly authenticated and authorized.
- Device Health: Continuously monitoring and validating the security posture of devices accessing corporate resources.
- Access Control: Granting access to services and data based on user identities, device health, and other contextual factors.
- Service Health: Continuously monitoring and securing the health of corporate services and applications.
Perception Point’s Advanced Browser Security
- Perception Point’s Advanced Browser Security provides enterprise-grade security for standard web browsers, combining:
- Advanced Threat Detection: Identifying and mitigating browser-based threats.
- Browser-Level Governance and DLP Controls: Enforcing security policies and data loss prevention measures within the browser environment.
- Managed Incident Response Service: Offering expert assistance in responding to and remediating security incidents.
Akamai’s Zero Trust Implementation Journey
- Akamai’s zero trust implementation journey involved:
- Securing Admin Accounts: Implementing robust authentication and access controls for administrative accounts.
- Device-Based Authentication: Leveraging device-based authentication mechanisms for user access.
- CDN-Based Single Sign-On (SSO): Integrating applications with a Content Delivery Network (CDN)-based SSO service for secure access.
DoD’s Zero Trust Strategy and Implementation
- The Department of Defense (DoD) is focused on:
- Developing a dod zero trust strategy and Framework: Outlining the strategic vision, principles, and goals for zero trust implementation.
- Building a Zero Trust Portfolio Management Office: Establishing a dedicated office to oversee and coordinate zero trust initiatives across the DoD.
- Key aspects of the dod zero trust strategy include:
- Treating All Users as Potential Threats: Denying access by default and granting access only after proper authentication and authorization.
- Minimum Access Principle: Allowing users only the minimum access required to perform their job functions.
- Four Strategic Goals: Promoting a zero trust culture, securing DoD information systems, accelerating zero trust technologies, and enabling zero trust capabilities.
- 45 Capabilities and 152 Activities: Outlining specific capabilities and activities to achieve the target level of zero trust by FY27.
- Zero Trust Capability Roadmap: Describing the sequencing and timeline for implementing zero trust capabilities.
- Three Courses of Action: Brownfield legacy transformation, commercial cloud options, and a government-designed native zero-trust cloud.
learn more about 7 Reasons Why You Need Managed IT services
- Key implementation challenges include:
- Leveraging Existing Investments: Integrating zero trust with existing security investments and technologies.
- Technology Integration: Ensuring seamless integration of various zero-trust technologies and solutions.
- User Experience Impact: Minimizing potential disruptions to user experience during the transition.
- Organizational Understanding: Fostering a common understanding of zero trust principles across the organization.
- Implementation guidance emphasizes:
- Focusing on Policy, Architecture, and Shared Services: Adopting a holistic approach beyond just technology.
- Integrating with Other Cybersecurity Disciplines: Aligning zero trust with other cybersecurity practices and frameworks.
- Translating Capabilities into System Requirements: Ensuring zero trust capabilities are properly reflected in system security requirements.
- Adequate Funding: Allocating sufficient resources for successful zero trust implementation.
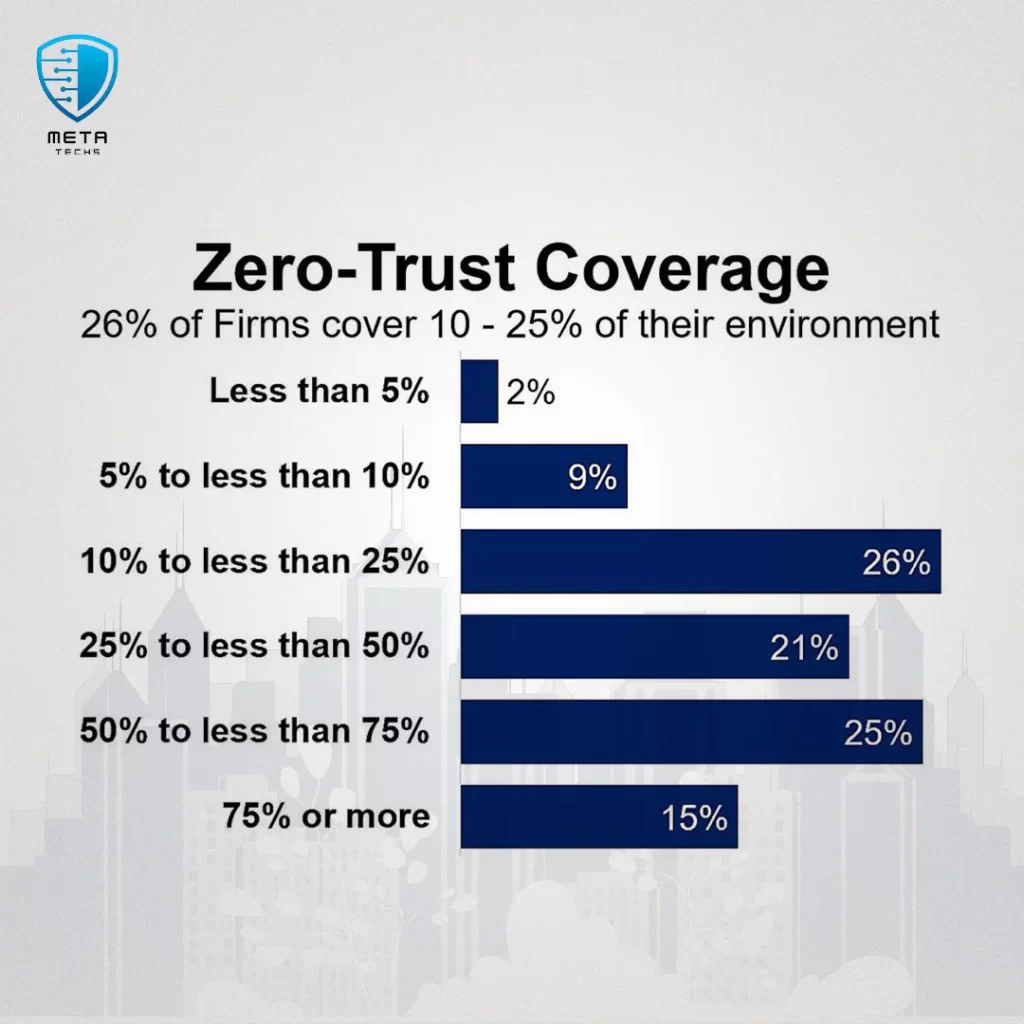
Percentage of Environment to Cover With Zero-Trust
Determining the Appropriate Scope
- Implementing a zero-trust strategy across an entire organization can be a daunting task, especially for large enterprises with complex IT environments. Industry reports suggest that most organizations typically address half or less of their environment when adopting a zero-trust approach.
- The percentage of the environment to be covered by zero trust depends on various factors, including:
- The organization’s risk appetite and security requirements
- The criticality of the assets and data to be protected
- The complexity of the existing infrastructure and applications
- The available resources and budget for the implementation
Prioritizing Critical Assets
- It is recommended to start by prioritizing the most critical assets and high-risk areas for zero-trust implementation. This could include:
- Sensitive data repositories
- High-value applications and services
- Systems handling sensitive or regulated data (e.g., financial, healthcare, or government)
- External-facing applications and services
- By focusing on these critical areas first, organizations can effectively mitigate the most significant risks and demonstrate the value of the zero-trust approach.
Gradual Expansion
- Once the initial implementation is successful, organizations can gradually expand the zero-trust strategy to encompass a larger portion of their environment. This iterative approach allows for:
- Refining policies and procedures based on lessons learned.
- Addressing challenges and issues identified during the initial rollout.
- Ensuring minimal disruption to ongoing operations and user productivity
- The pace of expansion should be determined by factors such as available resources, organizational readiness, and the complexity of the remaining systems and applications.
Balancing Security and Productivity
- While zero-trust implementation is desirable, it is essential to strike a balance between security and productivity. Overly restrictive access controls or disruptive changes can negatively impact user experience and operational efficiency.
- Organizations should involve end-users, administrators, and stakeholders throughout the implementation process to gather feedback and make necessary adjustments to minimize potential disruptions.
Continuous Monitoring and Adaptation
- Adopting a zero-trust strategy is an ongoing process that requires continuous monitoring, evaluation, and adaptation. As the organization’s environment evolves, new threats emerge, and user needs change, the zero-trust policies and controls must be updated accordingly.
- Establishing a dedicated team or governance structure to oversee the zero-trust implementation and maintenance can help ensure consistent application of policies and timely adaptation to changing requirements.
What is an example of a zero-trust policy?
Zero Trust Policy Examples
- Least Privilege Access Policy:
- Grant users and devices the minimum access required to perform their tasks, and no more.
- Continuously verify and re-evaluate access privileges based on user behavior, device posture, and other contextual factors.
- Revoke access immediately when it is no longer needed or when anomalies are detected.
- Multi-Factor Authentication (MFA) Policy:
- Require multi-factor authentication for all users, devices, and applications, regardless of their location or network.
- Implement risk-based MFA, where the number and strength of authentication factors required depend on the user’s risk profile and the sensitivity of the resource being accessed.
- Continuously monitor and analyze user behavior and device posture to detect potential threats and adjust authentication requirements accordingly.
- Micro-Segmentation Policy:
- Divide the network into smaller, isolated segments or zones based on user roles, resource types, or data sensitivity.
- Restrict lateral movement and communication between segments by default, allowing only authorized and encrypted traffic to flow between them.
- Implement granular access controls and monitoring mechanisms within each segment to detect and prevent unauthorized access or activities.
- Remote Access Policy:
- Enforce strict access controls and security measures for remote users and devices accessing corporate resources.
- Require secure virtual private network (VPN) connections or zero trust network access (ZTNA) solutions for remote access.
- Continuously monitor and validate the security posture of remote devices, and revoke access if anomalies or threats are detected.
Conclusion
The Zero Trust security model represents a significant shift in how organizations approach cybersecurity. By eliminating the concept of a trusted network and focusing on continuous verification and least privilege access, Zero Trust provides a robust defense against modern cyber threats. While implementing a comprehensive Zero Trust strategy across an entire organization is a complex undertaking, the benefits of enhanced visibility, continuous monitoring, and prevention of data breaches and lateral movement make it a worthwhile endeavor.
MetaTechs Cybersecurity offers protection against cybercriminals, safeguarding personal information and mitigating threats from the dark web. By being informed and taking appropriate precautions, individuals and organizations can navigate the digital landscape, including the definition of the dark web, with confidence and security.
FAQs
1. What is the DoD Zero Trust Strategy? The Department of Defense (dod zero trust strategy) introduced its formal Zero Trust Strategy in October 2022. This strategy serves as a security framework aimed at guiding the DoD towards achieving Zero Trust. It sets forth strategic objectives that include adopting a Zero Trust culture, defending DoD Information Systems, accelerating technology implementation, and establishing enabling conditions for Zero Trust.
2. How can a Zero Trust strategy be implemented? To implement a Zero Trust strategy, one must:
- Define the attack surface.
- Implement controls to manage network traffic.
- Design the architecture of a zero-trust network.
- Develop a zero trust policy that evaluates who, what, when, where, why, and how regarding individuals and systems seeking access to network areas.
3. What are the seven pillars of Zero Trust according to the DoD? The dod zero trust strategy (ZT) security model within the DoD is structured around seven core pillars that collectively define the agency’s cybersecurity stance. These pillars are:
- User
- Device
- Network & Environment
- Application & Workload
- Data
- Automation & Orchestration
- Visibility & Analytics
4. What is the five-step methodology for implementing Zero Trust? Implementing dod zero zero-trust strategy can be approached through a five-step methodology:
- The transition from focusing on the Threat Surface to the Protect Surface, as the concept of a threat surface is becoming less relevant in modern IT contexts.
- Map out Transaction Flows.
- Architect a Zero Trust Network.
- Develop a Zero Trust Policy.
- Continuously Monitor and Maintain the network.







